Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!

A flexible, future-ready encryption framework that generates secure cryptographic keys from diverse data sources—seamlessly adaptable across industries like secure communications, blockchain, and IoT, making it a powerful investment in the growing cybersecurity market.
Using advanced algorithmic, statistical, and rule-based methods, our framework creates truly random keys that are virtually impossible to predict—delivering stronger protection and a clear edge over traditional encryption.
Our multi-layered, modular encryption architecture lets organizations customize key generation to their exact needs—whether drawing from real-time sensor data, user behavior, or enterprise logs. This adaptability makes it a powerful B2B solution with extensive licensing and SaaS opportunities across industries.
Our flexible, extensible encryption technology transforms diverse data into secure keys, creating opportunities for partnerships in finance, defense, healthcare, and cloud infrastructure. Its adaptability delivers both cutting-edge security and strong commercial potential in markets demanding next-generation encryption.
To revolutionize data security by harnessing AI to create patternless cryptographic keys that deliver unmatched protection against evolving cyber threats.
To become the global leader in next-generation encryption, setting the standard for secure, adaptable, and future-proof data protection in the digital era.
We are committed to innovation, resilience, and trust—leveraging cutting-edge AI to ensure our clients’ most sensitive information remains secure, no matter how sophisticated the threat landscape becomes.
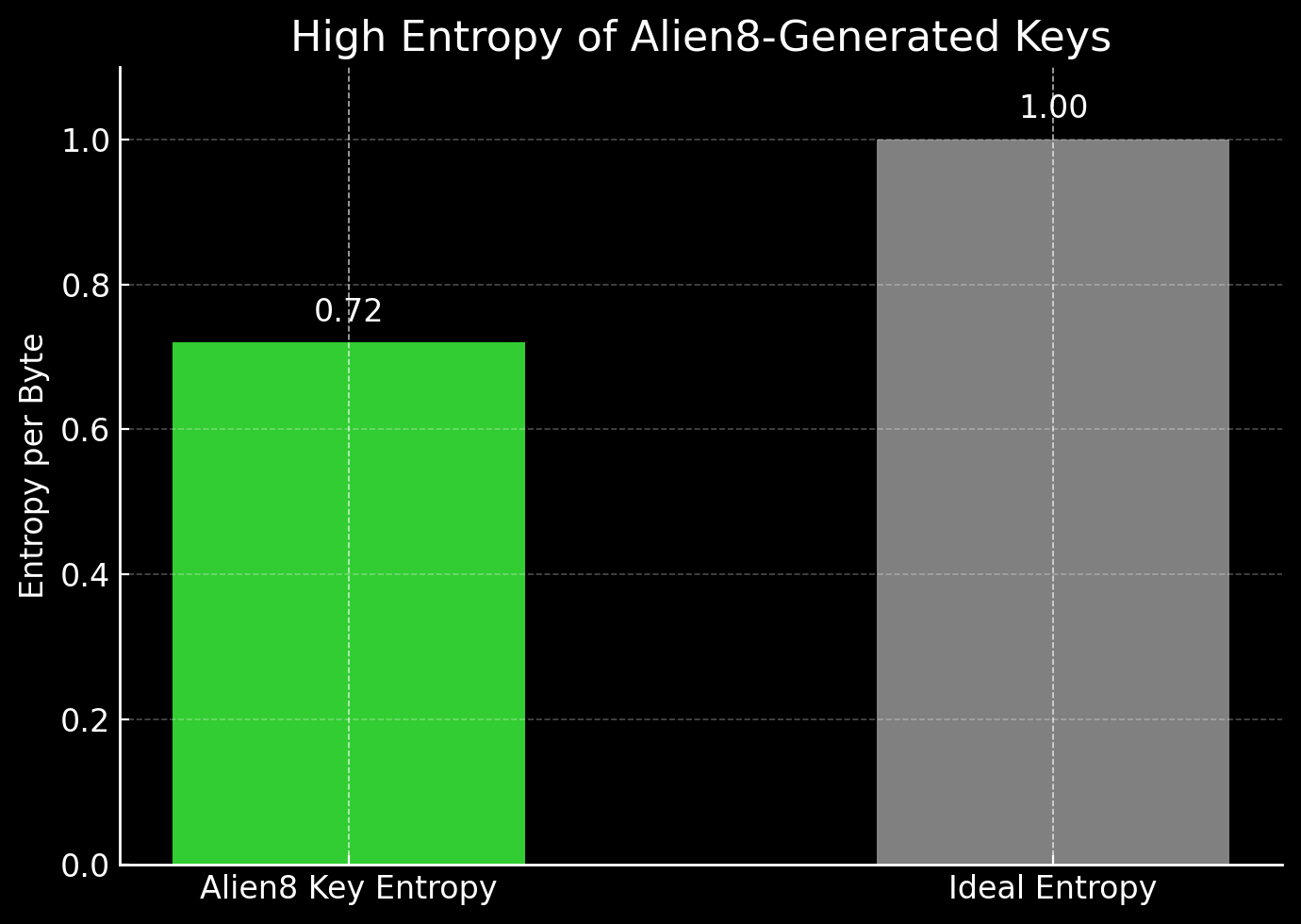
Our encryption keys achieve an impressive 0.72 entropy per byte, delivering near-perfect randomness for unmatched security and unpredictability
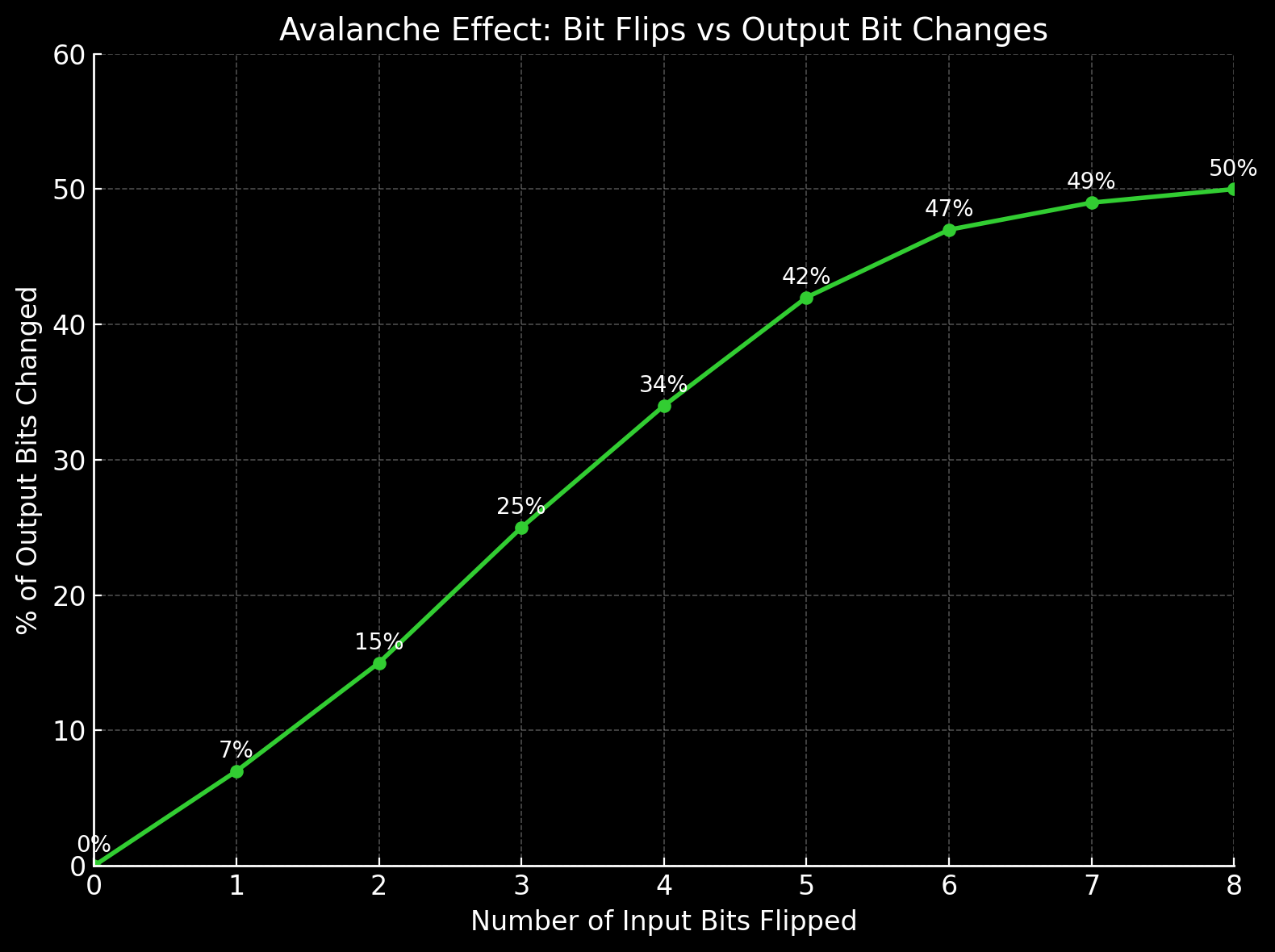
A single-bit change in the input triggers a ~50% shift in output, ensuring zero predictable patterns and maximum cryptographic strength
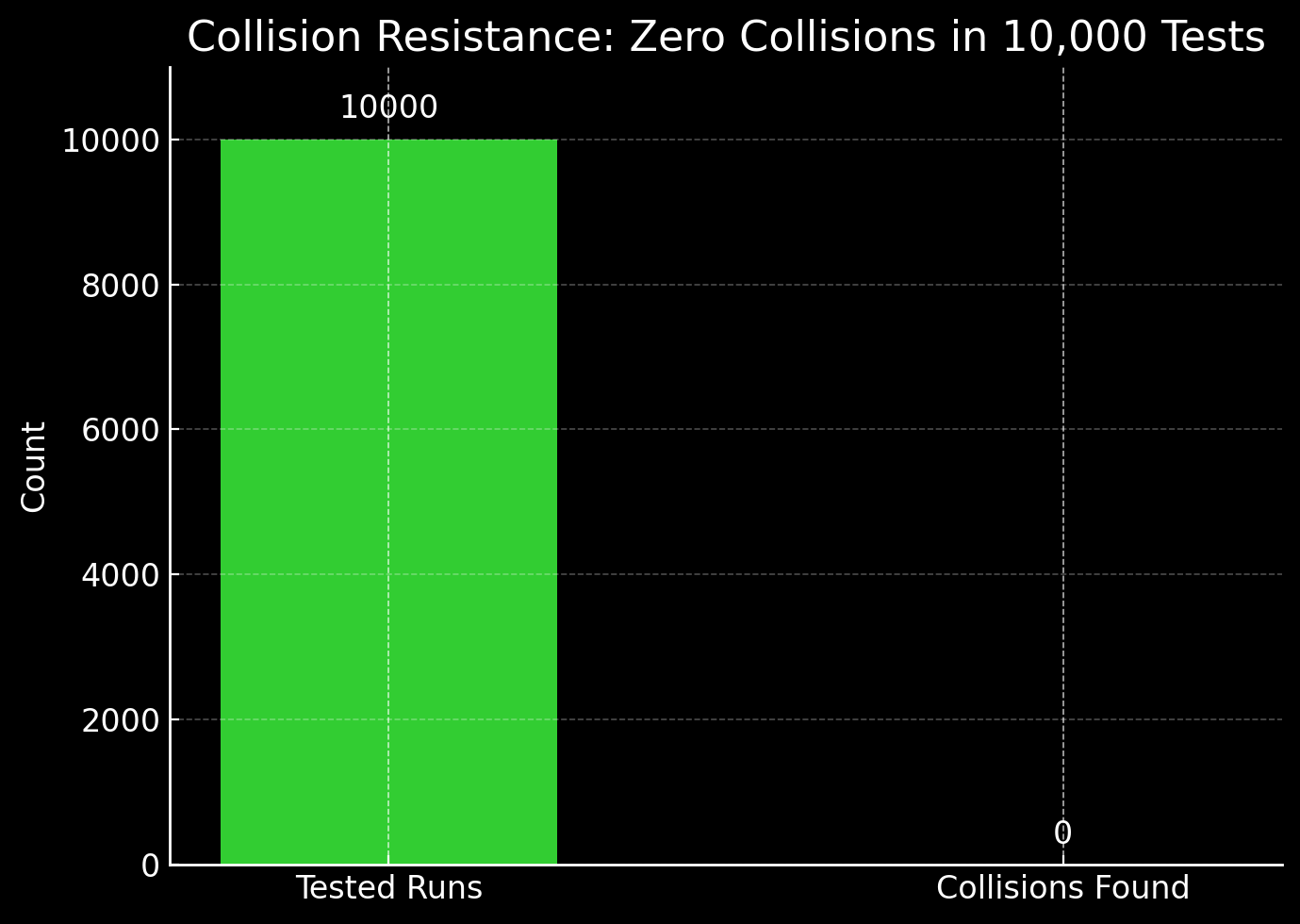
Across 10,000 test runs, no collisions were detected, reinforcing the uniqueness and reliability of the keys
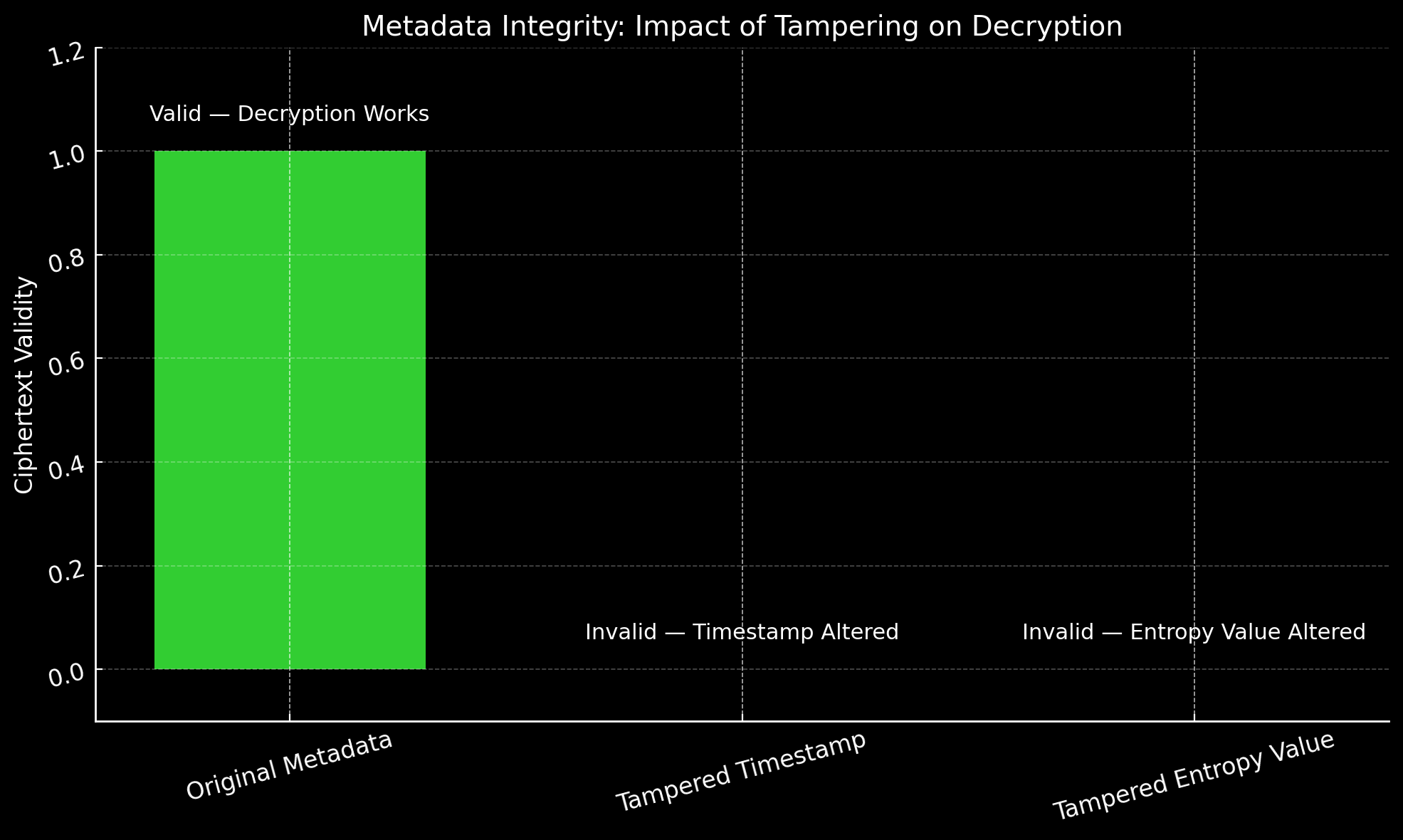
Even the slightest change to the metadata immediately renders the ciphertext useless, ensuring total protection against tampering.

Unlike SHA-3, a fixed algorithm built for general-purpose data, ALIEN8 provides adaptive, session-specific encryption with unique mappings, dual data stream integration, true system entropy, and bound metadata—delivering unmatched security beyond what SHA-3 can achieve.
Even if someone stole the entire code, without the exact audio input + metadata + system entropy bytes, they couldn’t recreate the key.

We start by securely initiating an AI-based key generation process, pulling from truly random data sources, and running them through our proprietary sequencing algorithm—creating the raw foundation for keys that are exceptionally difficult to crack.
Our system precisely analyzes the initial data stream using advanced classifications, extracting and recombining only the most critical features into a refined, high-entropy output—forming the ideal foundation for stronger, more resilient cryptographic keys.
The second data stream is processed through an AI-powered controller module, transforming it into a uniquely optimized, high-randomness representation—primed for secure and adaptable cryptographic key generation.
In the final stage, calculated values from the transformed data are mapped to create a highly secure, unique cryptographic key, which is then safely stored for authorized use.
Free
Let’s make something great work together. Get Free Quote
Take your brands to the next level with our expert web solutions Let’s get started today!
A KDF is a special kind of algorithm that takes some input (like a password, random data, or in our case, musical features) and produces a cryptographic key.
Far far away, behind the word mountains, far from the countries Vokalia and Consonantia, there live the blind texts. Separated they live in Bookmarksgrove right at the coast
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Lorem Ipsum has been the industry’s standard dummy text ever since the
domain@gmail.com
Copyright © 2025 All Rights Reserved.